Introduction
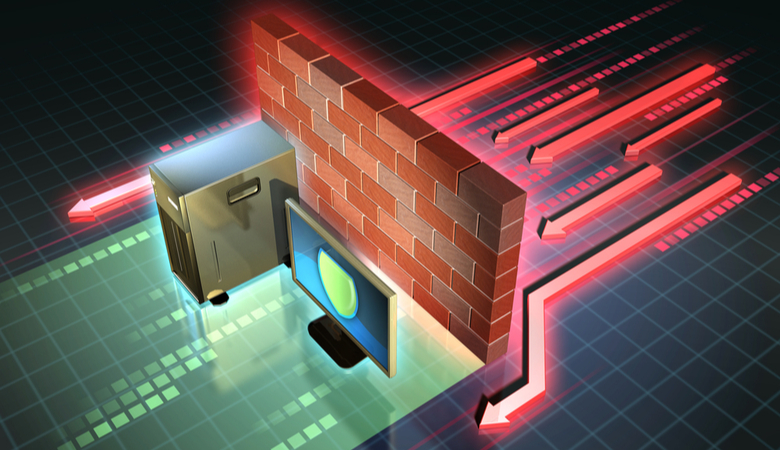
In today’s digitally connected world, cybersecurity is of paramount importance to safeguard sensitive information and critical systems from unauthorized access, data breaches, and cyber-attacks. Among the arsenal of cybersecurity tools, the firewall stands tall as one of the most fundamental and essential defenses. A firewall acts as a digital gatekeeper, monitoring and controlling the flow of network traffic to prevent malicious activities while allowing legitimate communication to flow unimpeded. This article delves into the evolution, working principles, types, and importance of firewalls in modern cybersecurity, along with its role in protecting organizations and individuals from cyber threats.
The Evolution of Firewalls
The concept of firewalls dates back to the early 1980s when the internet was in its infancy. In those early days, the focus was on creating a boundary between internal networks and the nascent public internet. The first-generation firewalls were relatively simple packet-filtering devices that inspected individual packets and determined whether to allow or deny them based on predefined rules.
Over time, firewalls evolved into more sophisticated stateful inspection firewalls. These firewalls could remember the state of connections and only allow traffic that belonged to established, legitimate connections. However, with the rise of advanced threats, such as malware and application-layer attacks, next-generation firewalls (NGFWs) emerged. NGFWs combine traditional packet filtering with deep-packet inspection, intrusion prevention systems (IPS), and application awareness to provide more comprehensive protection.
How Firewalls Work
Firewalls work on a set of predefined rules that dictate what network traffic is allowed and what is denied. When data packets arrive at a firewall, they undergo a series of checks against these rules. The rules can be based on factors like IP addresses, port numbers, protocols, or application signatures. If a packet matches an allowed rule, it is permitted to pass through the firewall to its destination. On the other hand, packets that don’t meet any allowed rules are either dropped or rejected, effectively denying them access.
Intrusion Prevention Systems (IPS) are an extension of firewalls that take a more proactive approach. IPS can inspect data packets in real-time, identifying and blocking potential threats before they reach their intended targets. IPS relies on signature-based detection, anomaly detection, and heuristics to identify malicious behavior.
Types of Firewalls
a. Packet Filtering Firewalls: These are the most basic type of firewalls that operate at the network layer (Layer 3) of the OSI model. They filter traffic based on source and destination IP addresses, port numbers, and protocols. While they are simple and efficient, they lack the ability to inspect data beyond the header, making them less effective against sophisticated attacks.
b. Stateful Inspection Firewalls: Also known as circuit-level firewalls, these firewalls keep track of the state of active connections and allow or deny traffic based on the connection’s state. They can understand whether a packet is part of an established connection or a new attempt to initiate a connection.
c. Application Layer Firewalls: Operating at the application layer (Layer 7), these firewalls can inspect the contents of data packets to identify specific applications or services. This deep inspection enables them to control access to applications and enforce more granular security policies.
d. Next-Generation Firewalls (NGFWs): As mentioned earlier, NGFWs combine the capabilities of traditional firewalls with intrusion prevention, application awareness, and deep-packet inspection. They offer a broader range of security features and can identify and block sophisticated threats.
Importance of Firewalls
a. Network Security: Firewalls act as a first line of defense, protecting networks from unauthorized access and cyber threats. By filtering and monitoring incoming and outgoing traffic, they prevent malicious activities and potential data breaches.
b. Application Security: Application layer firewalls and NGFWs help in securing specific applications by enforcing access control and preventing unauthorized data transfers.
c. Data Privacy: Firewalls contribute to data privacy by controlling the flow of data and ensuring that sensitive information is only accessible to authorized users.
d. Business Continuity: Firewall protection enhances business continuity by reducing the risk of cyber incidents and minimizing the potential impact of successful attacks.
e. Compliance Requirements: Many industry regulations and data protection laws require the implementation of firewalls as part of cybersecurity measures to protect sensitive data.
Firewall Challenges and Mitigations
a. Advanced Evasion Techniques: Some attackers use advanced evasion techniques to bypass traditional firewalls. To counter this, regular updates and maintenance of firewalls are essential.
b. Encryption: Encrypted traffic can be challenging for traditional firewalls to inspect. Deep-packet inspection and SSL/TLS decryption are potential solutions to tackle this challenge.
c. Insider Threats: Firewalls are ineffective against threats that originate from within the network. Combining firewall protection with other security measures, like user access controls and employee training, is crucial.
d. Scalability: Large organizations may face challenges in deploying and managing firewalls across vast networks. Firewalls must be scalable and flexible to adapt to evolving business needs.
Conclusion
In conclusion, firewalls continue to be the cornerstone of cybersecurity, protecting digital frontiers from a plethora of threats. Their evolution from simple packet filters to next-generation security devices showcases the ongoing efforts to combat ever-evolving cyber threats. The importance of firewalls cannot be overstated, as they play a vital role in maintaining network security, safeguarding sensitive data, and ensuring business continuity. As the cybersecurity landscape evolves, firewalls will continue to evolve, staying at the forefront of defending against emerging threats and maintaining the integrity of the digital realm.